Lacework & Revolgy
We connect with the best, so we can serve you best

We have partnered with Lacework to extend our portfolio of services. With Lacework’s unique data-driven cloud-native application protection platform, we are now able to offer solutions to embrace the security of your cloud technologies.
Your success is our mission
We help our clients make informed decisions and adopt best practices to get the most out of cloud technology. Listen to our customers, let their journeys inspire you.





What can our partnership
bring to you?
The partnership of Revolgy and Lacework creates a combination of services and solutions to meet the needs of fast-growing cloud-native companies. The benefits of combining the experience of certified AWS & GCP partner with leading-edge security solutions are key to success in the cloud.
Optimized cloud with full support of certified partner
Revolgy provides digital transformation services through a cloud infrastructure and online communication tools in the B2B segment. All from the incentives to start you projects to full cloud management including cost optimization and long-term support.
Cloud Security Assessment for free
Obtain a detailed security report and expert guidance within 24 hours; with a quick 30-minute deployment process to reveal all vulnerabilities in your cloud environment.

Podcast
Cloud Do You Do, Lacework?
In this episode, we discuss cloud security from A to Z with Tomas Lempera and Ivo Schoenamaker. Listen to what they have to say about today’s security challenges and how to tackle them successfully.
listen to the podcastLacework’s platform capabilities
Build securely
Fix vulnerabilities and misconfigurations before they hit production. Add security checks early in development, including infrastructure as code (IaC) scanning. Empower developers to scan locally, in registries, and CI/CD while building, at scale.
Prioritize risks
Deploy agentlessly to understand cloud risks in minutes. Get instant visibility into what’s deployed, how it’s configured, and pinpoint vulnerabilities and misconfigurations. Lacework scans everything – workloads, container images, hosts, and language libraries – so no secret can hide.
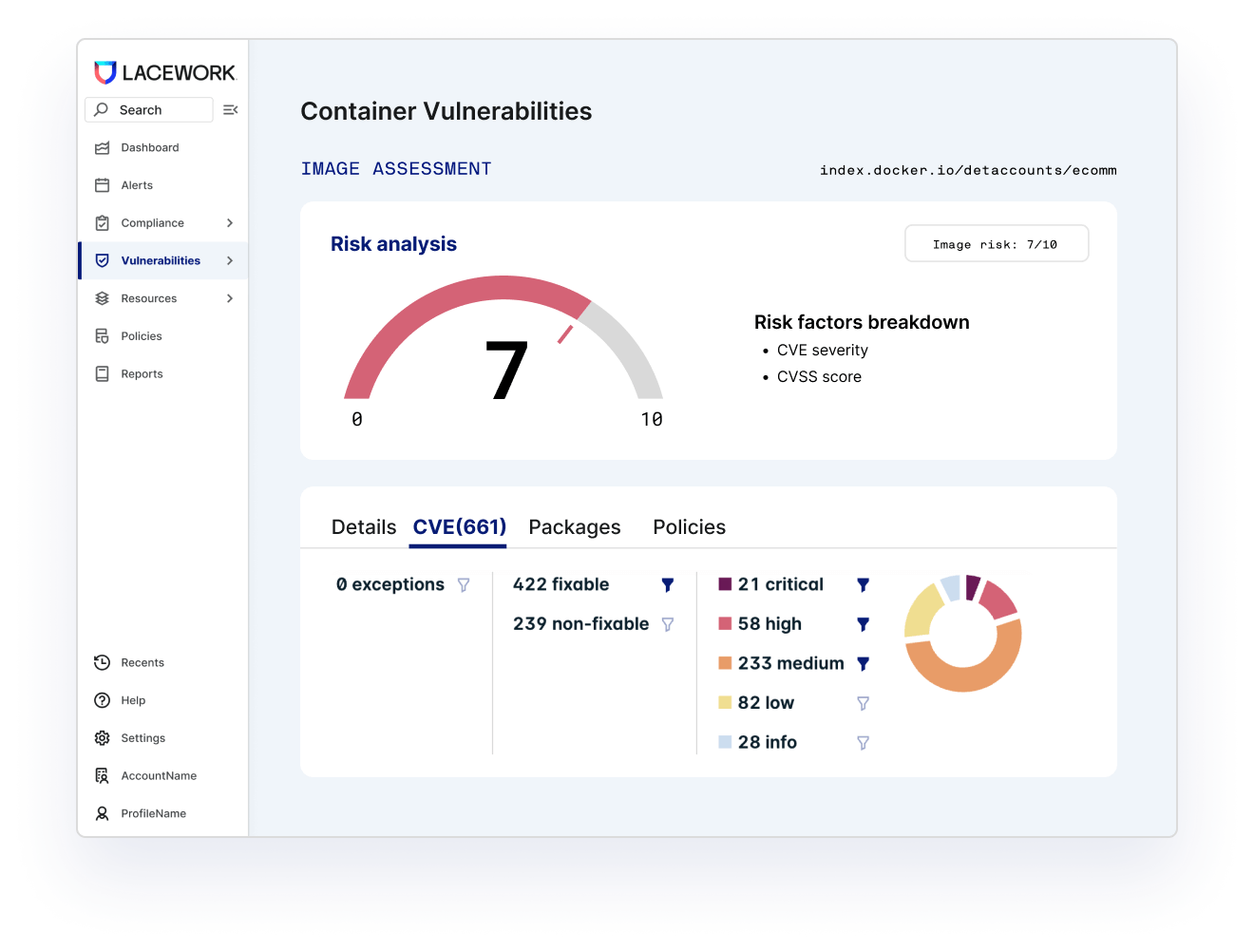
See attack paths
Tie together risk factors — vulnerabilities, misconfigurations, network reachability, secrets, and more — to see how attackers can compromise your cloud. Automatically connect with insights into what’s happening in runtime to prioritize critical risks, investigate faster, and even see suggestions for remediation.
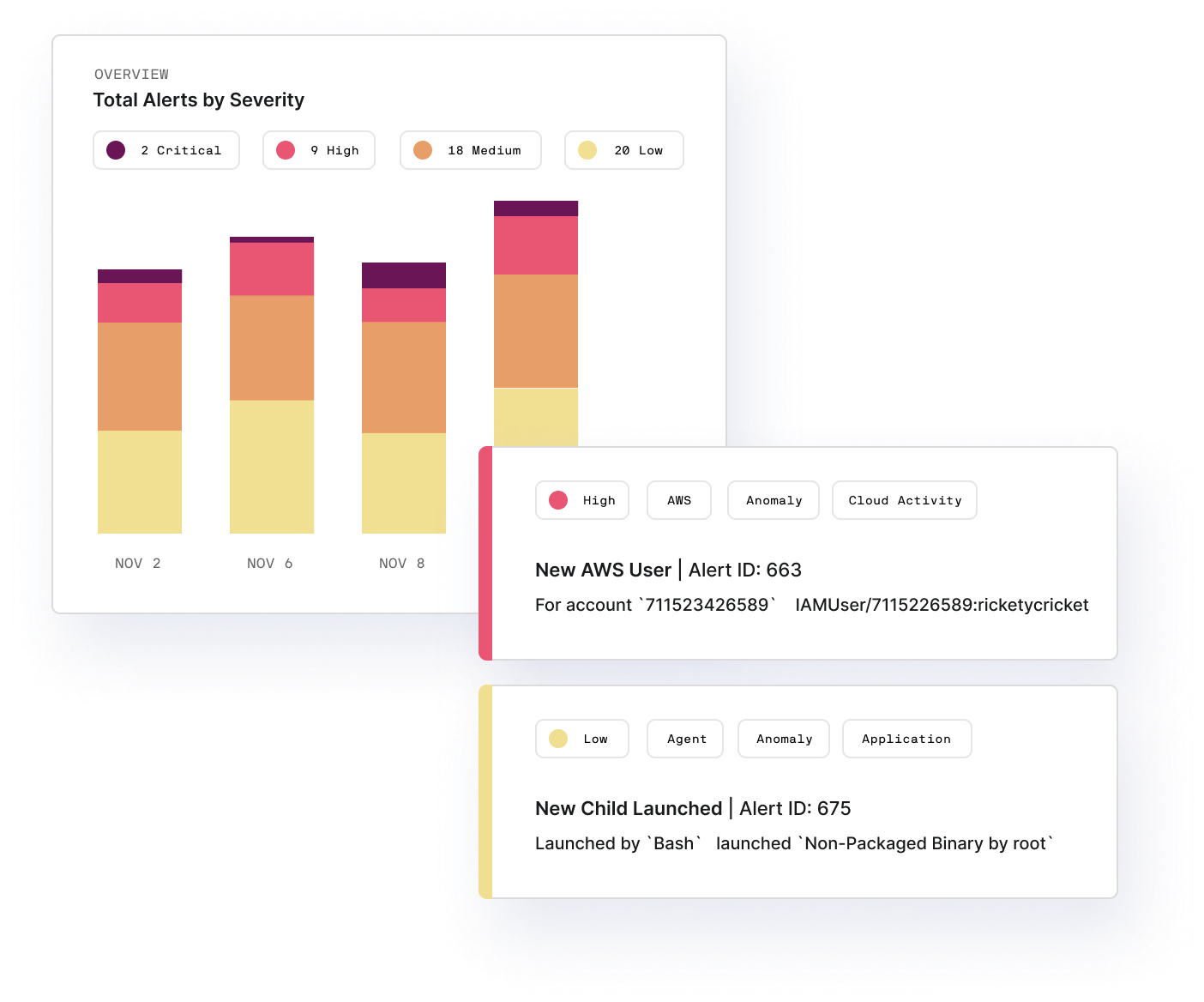
Monitor activity
Lacework’s patented Polygraph® technology continuously learns your normal to root out suspicious and unusual behavior. Data-driven monitoring reveals compromise and the resulting blast radius. Rich context helps you quickly understand what happened, how, and where to fix it. Their patented approach not only automates threat detection but can also significantly reduce your SIEM ingest costs.
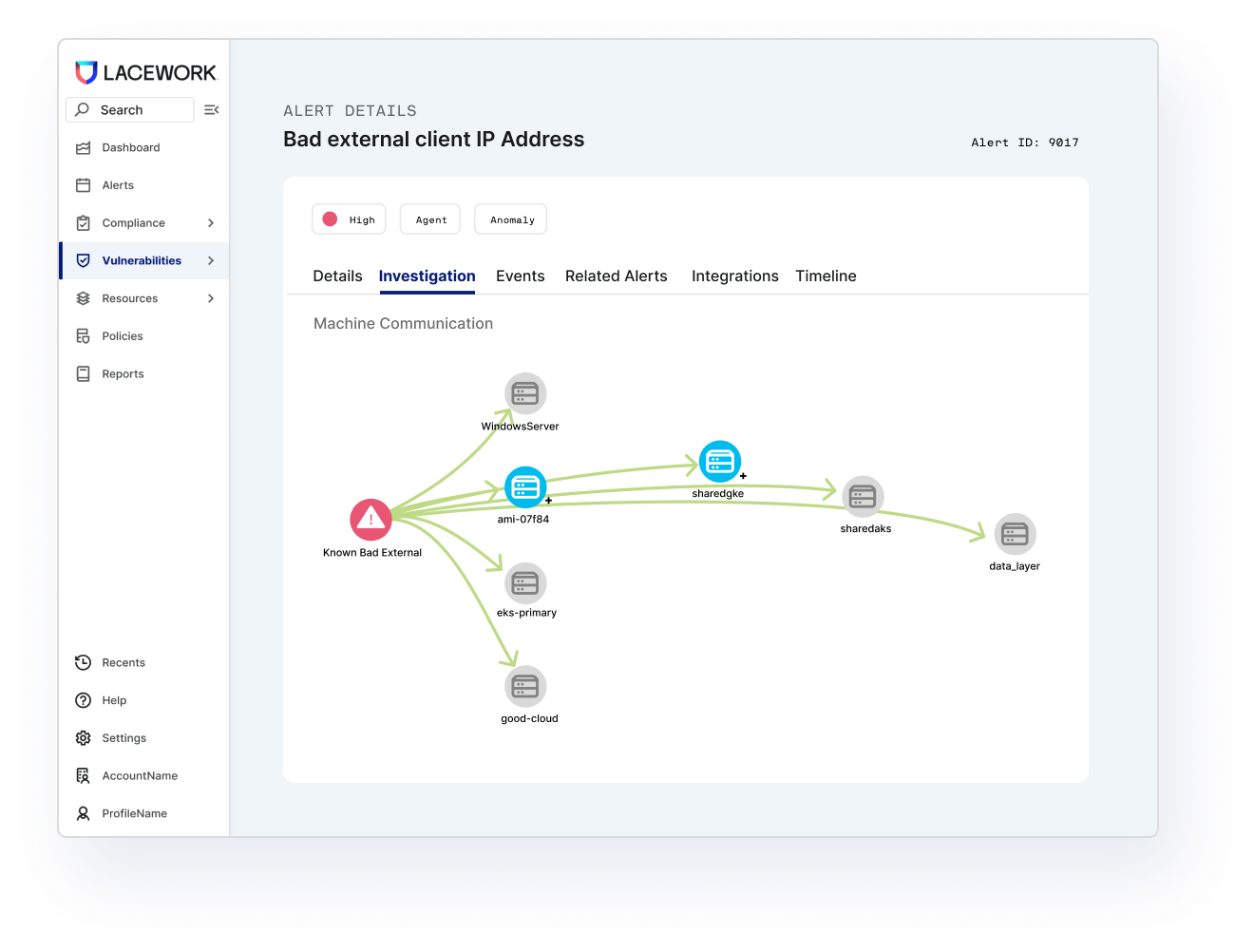
Secure workloads
Continuously protect critical applications and environments with Lacework’s workload and container security agent. Find new risks lurking in production and understand changes in behavior. Their data-driven approach connects the dots to detect known and unknown threats – even zero-day attacks. And do it all automatically without endless rule writing and deep security expertise required.
